If you're looking to centralize security for multiple AWS accounts, then look no further than Megallan Health's architecture. Sure, there are a few areas that could be improved, but it's still a great starting point. This architecture was featured on the "This is My Architecture" series from AWS.
Check out the following design:
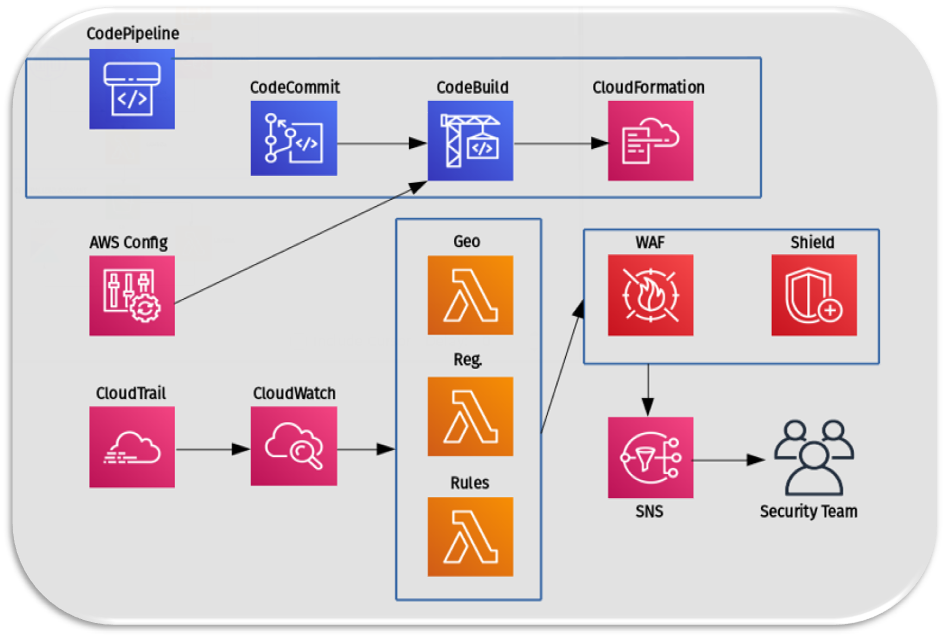
Now, let's talk about the key design decisions:
- CodePipeline is used to commit code.
- CodeBuild is used to execute the committed code and ultimately generate CloudFormation templates to control all the accounts.
- CloudTrail is used to feed in rules for CloudWatch events. For example: which events to listen to.
- There are three main functions of the security lambdas:
- Geomatch Lambda: This ensures that any region that the security team deems unsafe will be restricted from accessing the site.
- Registration/Association Lambda: This makes sure that new AWS resources are protected. For example, if an ALB or ELB instance is created, it will trigger the registration function and assume a role on the account it was created from. This function checks if the new resource was updated or added and if it's protected by WAF. If it isn't, then it adds it. Conversely, if the resource was deprecated, then WAF removes the resource from the list to accurately depict what's protected and what's not.
- Custom Rules Applicator Lambda: This allows the security team to create custom rules for exceptions. The cool thing about this lambda is that it's all code and allows the application team to have an audit trail of who created the exception, why it was created, and who approved the code commit. It helps isolate and delegate responsibility.
- Any time any event happens, AWS WAF or AWS Shield will trigger an SNS notification, alerting the security team.
Looking back, we could use AWS Firewall Manager to configure and manage these WAF rules across all accounts and applications. I'm sure the team has updated the architecture by now and could very well be using Firewall Manager.
Reference: This is My Architecture, AWS